The growing number of mobile devices requires some sort of mobile device management policy to be in place. Now there are different approaches to enforce such a policy, there are some software vendors offering more or less sophisticated tools and there is Exchange 2010 which comes with basic device management capabilities built-in.
If a mobile device connects to an Exchange Server the following sequence evaluates the access state of the device (from TechNet: http://technet.microsoft.com/en-us/library/ff959225.aspx)
- Is the mobile device authenticated? If not, challenge the mobile device for the correct credentials. Otherwise, go on to the next step.
- Is Exchange ActiveSync enabled for the current user? If not, return an "access restricted" error to the device. Otherwise, go on to the next step.
- Are the mobile policy enforcement criteria met by the current mobile device? If not, block access. Otherwise, go on to the next step.
- Is this mobile device blocked by a personal exemption for the user? If so, block access. Otherwise, go on to the next step.
- Is this mobile device allowed by a personal exemption for the user? If so, grant full access. Otherwise, go on to the next step.
- Is this mobile device blocked by a device access rule? If so, block access. Otherwise, go on to the next step.
- Is this mobile device quarantined by a device access rule? If so, quarantine the device. Otherwise, go on to the next step.
- Is this mobile device allowed by a device access rule? If so, grant full access. Otherwise, go on to the next step.
- Apply the default access state per the Exchange ActiveSync organizational settings. This grants access, blocks access, or quarantines the current device, depending on the organizational settings.
Default Access State
The last step in the above list determines the ‘default access level’ organizational setting. This setting defaults to ‘Allow’ so if no other device access rules are configured, all ActiveSync devices (which meet enforcement criteria) are allowed. That means, any user with an ActiveSync enabled mailbox (another default) is able to connect up to 10 devices using ActiveSync.
To change this behavior the ‘default access level’ setting can be modified using the ‘Set-ActiveSyncOrganizationSettings’ cmdlet. Other than ‘Allow’ this can be set to ‘Quarantine’ or ‘Block’.
Quarantine: Enables devices to connect to the Server but grants only limited access to the device. Users will be able to add content to their calendar, tasks and notes folders, however no content can be retrieved from the server. The user will receive an email stating that the mobile device has been quarantined, that email can be retrieved by the mobile device and will be available in the users mailbox through Outlook and OWA. If a device is quarantined an administrative email address is notified too, so that they can decide to allow or block the device.
An admin (or any user with the required privileges) who receives the notification can use the Exchange Control Panel to allow or block the device:
Devices listed in a users ‘ActiveSyncAllowedDeviceIDs’ attribute are allowed.
Block: Simply blocks all new or unknown devices. Devices listed in a users ‘ActiveSyncAllowedDeviceIDs’ attribute are allowed.
If users are already using ActiveSync to access their mailboxes the Exchange Management Shell can be used to add the DeviceID of currently used ActiveSync devices to the ActiveSyncAllowedDeviceIDs property.
Set-ActiveSyncOrganizationSettings
The following command sets the recipient of the admin notification to [email protected]. Every time a device is quarantined that email address is notified.
Set-ActiveSyncOrganizationSettings –AdminMailRecipients [email protected]
The following command sets the ‘default access state’ to quarantine.
Set-ActiveSyncOrganizationSettings –DefaultAccessLevel Quarantine
Need to scale? Try Device Access Rules!
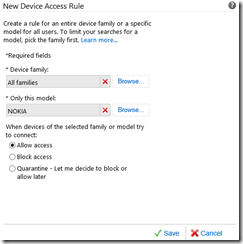
Manual approval might not work for environments with many users or when users change their mobile devices frequently. Device Access Rules can be used to allow or block devices based on Family or Model so that users can connect approved device types without the need to be manually allowed by an admin:
Using Device Access Rules allows for some amount of scalability, even though it’s not perfect – it comes with Exchange.
so long,
tom