In this post, we started out by deploying the VCSA to a new environment, today we'll see how to join the VCSA to an Active Directory domain and authenticate using domain accounts.
Prepare
To join a domain we need the distinguished name of the organizational unit where we want the VCSA's computer object to be created, as well as an account with the required permissions to join a machine to the domain.
To get the DN use your tool of choice, like PowerShell:
Get-ADOrganizationalUnit -Filter {Name -like "servers"} | Select-Object -ExpandProperty DistinguishedName
Before joining the vCenter Server Appliance to the domain, make sure DNS is working perfectly, that includes reverse lookup.
Join
Now sign-in to the vCenter using the local SSO domain created during setup and go to Administration/System Configuration/Nodes. Select the VCSA from the list of Nodes and in the right pane, go to Manage/Active Directory and click the "Join" button on the right.
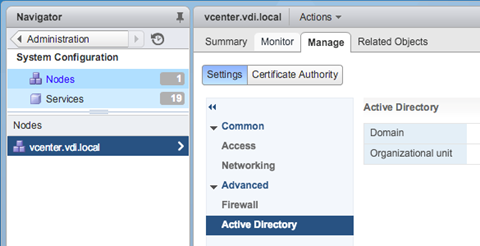
Specify the domain name and DN of the organizational unit as well as the credentials to use.
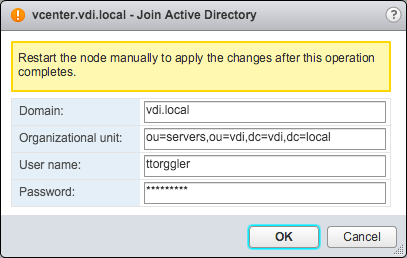
After joining the domain, a restart is required. To perform a restart, either use SSH or use the "Reboot" button in the "Actions" menu.
Once the VCSA is restarted we can see that a Computer object has been created in AD. Now we log-in again, still using the local account, and go to Administration/Configuration where we select "Identity Sources" in the right pane, using the "+" button, add a new Identity Source.
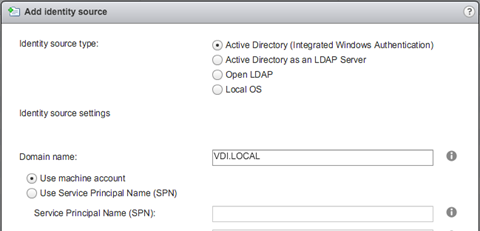
Configure Permissions
Once the Identity Source has been added, we can configure roles and permissions for AD accounts. This can be done using Administration/Global Permissions. Using the "+" button, we assign an AD user or group to a vCenter Role.
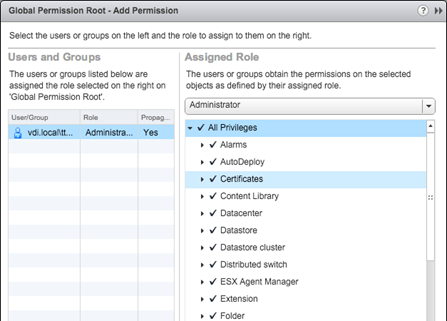
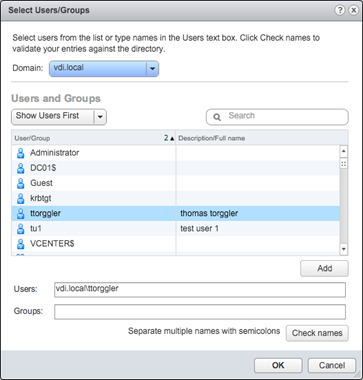
Alternatively, we can add AD users or groups to the preconfigured groups that can be found in the "Single Sign-On" section of the Administration menu.
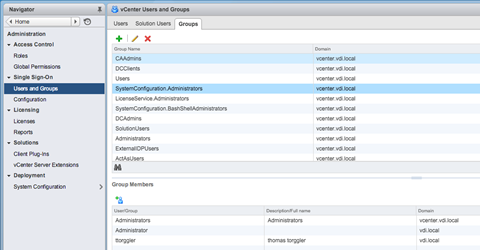
Verify
Finally we can log-out of the local admin account and log-in using our AD user, which should be able to access resources, as specified by the assigned roles. Note: Users with no assigned roles will also be able to log-in, obviously they won't see any objects.
Troubleshoot
Now if some of the steps don't work, for example you cannot log-in or you cannot access AD users or groups in the configuration, double-check DNS and have a look at the following log files:
/var/log/vmware/sso/vmware-sts-idmd.log
/storage/log/vmware/sso/ssoAdminServer.log
I got "Cannot load the users for the selected domain" in the Web Client and found the following lines in the above mentioned logs:
Failed to get non-GC connection to domain
com.vmware.identity.idm.IDMException: Failed to establish server connection