We had an interesting problem at work recently, as the solution was a little complex I decided to write about it here. So, as the title suggests, we are talking Wireless networking, authentication and Mac OS X today. It’ll be fun, trust me :)
Some prerequisites: We use EAP-TLS as the authentication protocol for WiFi and SCEP for certificate enrollment. I’ve written about SCEP before, in a different context, though. We also use the iPhone Configuration Utility to deploy configurations to devices, more on that later.
The Problem
We join our MACs to the Active Directory domain and want our users to be able to login using their domain credentials. Obviously you need some sort of connectivity to the AD in order to login, we used to configure Wireless Networks as “System Profile” in OS X in the past. Unfortunately, that GUI went away in more recent versions of that operating system.
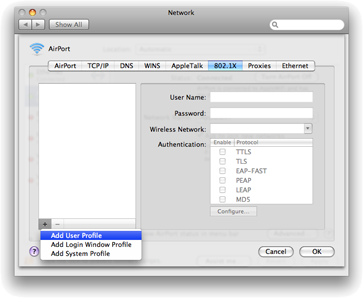
This is a screenshot of 10.5, simple enough. As we tried to configure that same thing on 10.8, though, we realized that this little option was gone. All Wi-Fi networks would be started AFTER the used login, no AD login was possible. Oops.
After scratching our heads for a while, we found a workaround other than installing Windows ;)
The Solution
iPhone Configuration Utility was used ever since we had the requirement to connect iOS devices to the wireless network, it can be used to create configuration files that can be deployed to iOS devices. It has been possible for some time to deploy these same configuration files to OS X, too. As they are simple XML files, we took a deeper look into them. Wwith some help from Google we found that we could change the Wi-Fi payload to be a “System Profile” instead of a “User Profile”, and thus be started BEFORE user login.
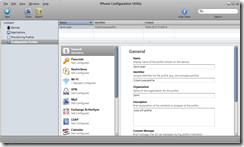
So, first thing is to create a configuration profile using iPhone Configuration Utility.
Choose a name, identifier and description for the profile.
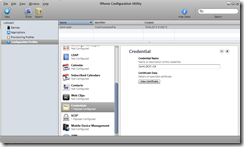
Add the certification authorities certificate, so we trust certificates issued by our internal CA.
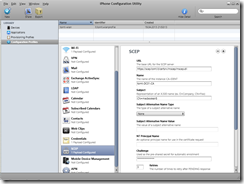
Configure SCEP, the iPhone or MAC is going to connect to the SCEP URL to enroll a certificate using the specified subject.
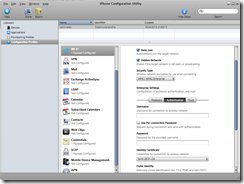
Add the Wi-Fi payload, specifying the SSID and authentication protocol. As we use EAP-TLS we use the SCEP certificate to authenticate.
Once the profiles is configured, export it:
We get a .mobileconfig file from the export, it can be edited using a simple text editor. Here comes the fun part, we have to add the following lines to the configuration file:
<key>SetupModes</key>
<array>
<string>System</string>
</array>
<key>PayloadScope</key>
<string>System</string>
This part goes just underneath the PayloadOrganization in the AutoJoin section.
And we have to change “Configuration” at the very end of the file from:
<key>PayloadType</key>
<string>Configuration</string>
to “SystemConfiguration”:
<key>PayloadType</key>
<string>SystemConfiguration</string>
As it is quite important where you change/add the lines, I’ll paste a complete file for reference.
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>PayloadContent</key>
<array>
<dict>
<key>AutoJoin</key>
<true/>
<key>EAPClientConfiguration</key>
<dict>
<key>AcceptEAPTypes</key>
<array>
<integer>13</integer>
</array>
<key>EAPFASTProvisionPAC</key>
<false/>
<key>EAPFASTProvisionPACAnonymously</key>
<false/>
<key>EAPFASTUsePAC</key>
<false/>
<key>PayloadCertificateAnchorUUID</key>
<array>
<string>25800C8A-A389-4598-A3C4-F5569A4D5273</string>
</array>
</dict>
<key>EncryptionType</key>
<string>WPA</string>
<key>HIDDEN_NETWORK</key>
<true/>
<key>PayloadCertificateUUID</key>
<string>40C2FC1D-D1AA-4BA6-B2A3-959B6BFF9EB1</string>
<key>PayloadDescription</key>
<string>Configures wireless connectivity settings.</string>
<key>PayloadDisplayName</key>
<string>WiFi (MYSSID)</string>
<key>PayloadIdentifier</key>
<string>it.tomt.wlanprofile.wifi1</string>
<key>PayloadOrganization</key>
<string>tomt</string>
<key>SetupModes</key>
<array>
<string>System</string>
</array>
<key>PayloadScope</key>
<string>System</string>
<key>PayloadType</key>
<string>com.apple.wifi.managed</string>
<key>PayloadUUID</key>
<string>2CD56B1A-068C-4F3C-AC43-9D4E2115260F</string>
<key>PayloadVersion</key>
<integer>1</integer>
<key>ProxyServer</key>
<string>proxy.ntsystems.it</string>
<key>ProxyServerPort</key>
<integer>8080</integer>
<key>ProxyType</key>
<string>Manual</string>
<key>SSID_STR</key>
<string>MYSSID</string>
</dict>
<dict>
<key>PayloadCertificateFileName</key>
<string>tomt-DC01-CA</string>
<key>PayloadContent</key>
<data>
MIIDYzCCAkugAwIBAgIQL1CM7d+PQrhAgO7UcdHbyDANBgkqhkiG
…
bnBODc20wZMRDAhWuA==
</data>
<key>PayloadDescription</key>
<string>Provides device authentication (certificate or identity).</string>
<key>PayloadDisplayName</key>
<string>tomt-DC01-CA</string>
<key>PayloadIdentifier</key>
<string>it.tomt.wlanprofile.credential2</string>
<key>PayloadOrganization</key>
<string>tomt</string>
<key>PayloadType</key>
<string>com.apple.security.root</string>
<key>PayloadUUID</key>
<string>25800C8A-A389-4598-A3C4-F5569A4D5273</string>
<key>PayloadVersion</key>
<integer>1</integer>
</dict>
<dict>
<key>PayloadContent</key>
<dict>
<key>Challenge</key>
<string>4F20EACEDE479165</string>
<key>Key Type</key>
<string>RSA</string>
<key>Key Usage</key>
<integer>0</integer>
<key>Keysize</key>
<integer>2048</integer>
<key>Name</key>
<string>tomt-DC01-CA</string>
<key>Retries</key>
<integer>3</integer>
<key>RetryDelay</key>
<integer>10</integer>
<key>Subject</key>
<array>
<array>
<array>
<string>CN</string>
<string>macbookair$</string>
</array>
</array>
</array>
<key>URL</key>
<string>https://scep.tomt.it/certsrv/mscep/mscep.dll</string>
</dict>
<key>PayloadDescription</key>
<string>Configures SCEP</string>
<key>PayloadDisplayName</key>
<string>SCEP (tomt-DC01-CA)</string>
<key>PayloadIdentifier</key>
<string>it.tomt.wlanprofile.scep3</string>
<key>PayloadOrganization</key>
<string>tomt</string>
<key>PayloadType</key>
<string>com.apple.security.scep</string>
<key>PayloadUUID</key>
<string>40C2FC1D-D1AA-4BA6-B2A3-959B6BFF9EB1</string>
<key>PayloadVersion</key>
<integer>1</integer>
</dict>
</array>
<key>PayloadDescription</key>
<string></string>
<key>PayloadDisplayName</key>
<string>tomt-wlan</string>
<key>PayloadIdentifier</key>
<string>it.tomt.wlanprofile</string>
<key>PayloadOrganization</key>
<string>tomt</string>
<key>PayloadRemovalDisallowed</key>
<false/>
<key>PayloadType</key>
<string>SystemConfiguration</string>
<key>PayloadUUID</key>
<string>B58A2BCB-7617-421B-B0C8-12DE22B5A2B1</string>
<key>PayloadVersion</key>
<integer>1</integer>
</dict>
</plist>
Now, if we copy that file to the MAC OS X machine, we can import the wireless configuration and it will be a system profile. Phew.
(In this case we need some sort of connectivity in order to enroll for a certificate over SCEP, this could be via LAN or an open guest Wi-Fi)
Summary
It might be though to get your head around this if EAP-TLS and SCEP are new, yet the same idea holds through for a Username/Password or even pre-shared key authentication protocol. The problem remains the same, Wi-Fi user profiles are started after the user logs on, rendering Active Directory logins impossible. We couldn’t find a solution to change that behavior without the iPhone Configuration Utility.
Would be happy to hear about others experiences with this stuff.
Special thanks to my mate @eduriz :)
tom