I decided to use Netscaler to publish my ADFS server to the internet instead of a dedicated server in the DMZ. I checked several blogs and the official Citrix documentation but this looked overloaded.
Citrix documentation: NetScaler as ADFS Proxy Deployment Guide - Citrix
Blogs: http://blogs.citrix.com/2015/05/29/adfs-v3-on-windows-server-2012-r2-with-netscaler/, http://cividan.blogspot.it/2015/02/use-citrix-netscaler-as-replacement-for.html
So I searched a way to:
- Publish ADFS to the Internet with URL filter
- Do not pre-authenticate with Netscaler (Customizing multiple pre-authentication Websites can be very time consuming per tenant)
- Modify the Header that ADFS server understands the request comes from external
There was no blog post that explained the whole configuration, so I decided to write down the required steps:
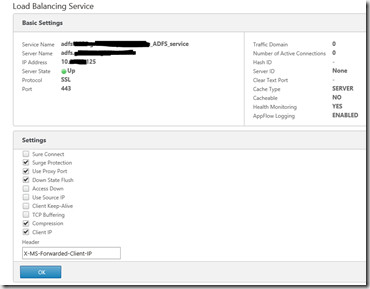
1. The service
First create the service and specify to forward the Client IP (Header: X-MS-Forwarded-Client-IP)
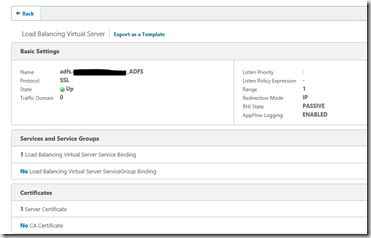
2. The vServer
Create the vServer not directly addressable to not trash an IP address and bind the certificate
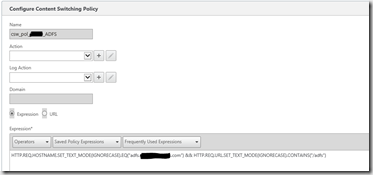
3. Content switch policy
Create a content switch policy to forward only /adfs and the exact hostname to the vServer
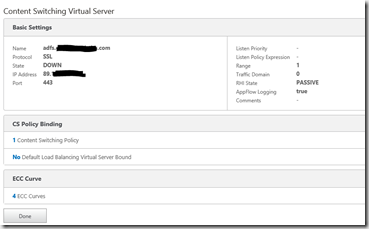
4. Content Switch vServer
Create the content switch vServer and apply the content switch policy
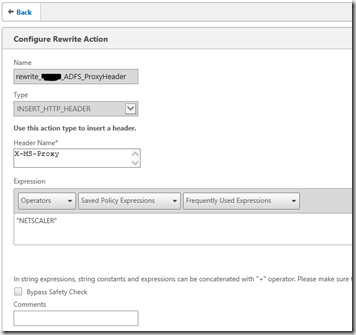
5. Rewrite Actions
You want to let the ADFS know that the request comes from extranet. So you can apply different authentication methods in the different zones. You have to add the header X-MS-Proxy to the request. Therefore you create a rewrite action
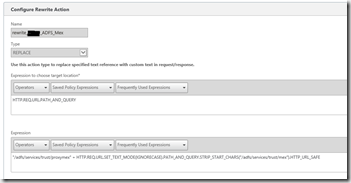
Create also a rewrite action to rewrite URL /mex
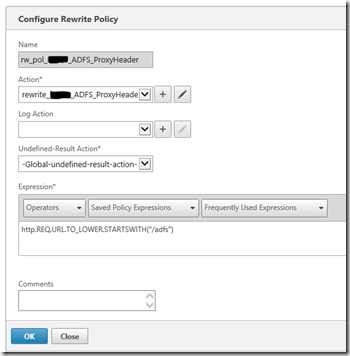
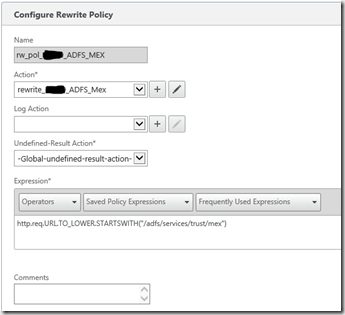
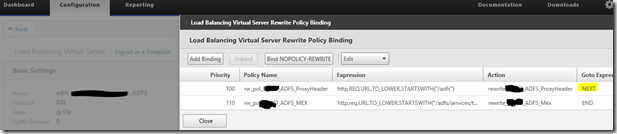
6. Rewrite Policy
7. Bind the Policies
Now bind the policies to the vServer. Both are rewrite policies for requests. Be careful with the GoTo expression to the Header transformation, this must be “NEXT”
8. The Monitor
ADFS has a probe check build in. If you check /adfs/probe you get a 200 message if everything is OK. Create the monitor and add it to the service
<p><a href="/assets/archive/image_684.png"><img width="265" height="339" title="image" style="border: 0px currentColor; padding-top: 0px; padding-right: 0px; padding-left: 0px; display: inline; background-image: none;" alt="image" src="/assets/archive/image_thumb_682.png" border="0"></a></p> <p> </p> <p>Netscaler configuration is done. You can test now the authentication if you access the URL <a href="https://portal.office.com">https://portal.office.com</a> through Netscaler. Then you will be redirected to the ADFS website for authentication:</p> <p><a href="/assets/archive/image_685.png"><img width="438" height="156" title="image" style="border: 0px currentColor; padding-top: 0px; padding-right: 0px; padding-left: 0px; display: inline; background-image: none;" alt="image" src="/assets/archive/image_thumb_683.png" border="0"></a></p> <p>For internal requests use split DNS to forward the authentication directly to the ADFS server and not to the Netscaler ADFS proxy. So the Proxy Header is missing and your client will use internal authentication.</p> <p>Stay tuned for my post series about configuring Exchange in Hybrid mode with Office 365.</p> <p>Greetings<br>ND</p>