The use of smartphones and other mobile email clients has been increasing for quite some time. With ActiveSync being one of the widest-used protocols comes the need to manage another set of devices. As users are forced to change their domain account’s passwords from time to time, some might forget to update their smartphones as well.
The Problem
So, as a user changes their password, the mobile device will continuously try to sync with a wrong set of credentials. Now depending on the rate at which it tries to sync, this might very well lock-out the users AD account, depending on the Domains Password Policy.
Another possibility to consider is an attacker who could create quite a disturbance by locking out accounts intentionally, using any published Web Site with Forms Base Authentication.
The Solution
Forefront TMG 2010 SP2 comes with a new feature, called AccountLockoutThreshold. Forefront TMG keeps track of failed logons and locks the account locally, after a specified amount of failures. After that, any other attempt to authenticate via TMG is not forwarded to Active Directory/LDAP, so that the users account does not get locked-out continuously .
The AccountLockoutThreshold feature is local to the Forefront TMG server, so if there is an array of publishing servers, it has to be configured on each of them. It can only be configured for Web Listeners using Forms Based Authentication.
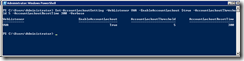
To configure AccountLockoutThreshold we need to use PowerShell, there is no GUI that exposes this setting. A great script to control the settings is available in the Script Center. So, we copy the script and save it to a *.ps1 file on the Desktop of the TMG Server, then we use dot-sourcing to load it into an administrative PowerShell session.
Example: I saved the script to AccountLockout.ps1 on the Desktop. Use “. .\Desktop\AccountLockout.ps1” to import the script.
The Get-AccountLockoutSetting cmdlet is used to retrieve the current settings.
The Set-AccountLockoutSetting cmdlet is used to configure the feature.
Example: I use “Set-AccountLockoutSetting -WebListener OWA -EnableAccountLockout $true -AccountLockoutThreshold 5 -AccountLockoutResetTime 300” to enable the AccountLockout feature, accounts will get locked out for 300 seconds if there are 5 consecutive failed attempts.
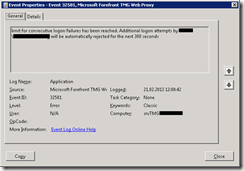
Once configured, the following event will be logged to the Application Log of the TMG server if an account gets locked out locally:
Source: Microsoft Forefront TMG Web Proxy
Event ID: 32581
Level: Error
Text: limit for consecutive logon failures has been reached. Additional logon attempts by domain.local\user.name will be automatically rejected for the next 300 seconds
Unfortunately TMG has been discontinued and is no longer available for customers, but for anyone already using it, this should help you dealing with Account Lockout Policies and ActiveSync devices.
so long,
tom